Identity and Access Management (IAM)
Key Risk Management Considerations
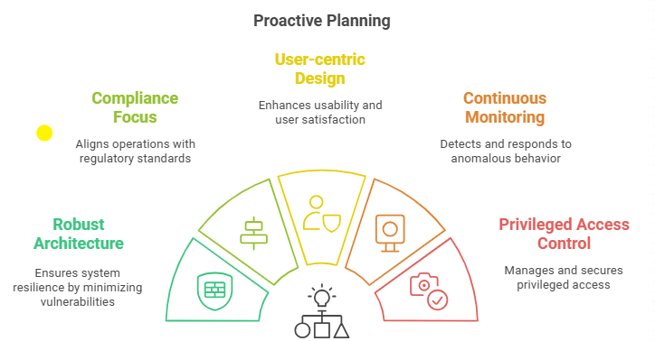
Proactive Planning: Thoroughly assess risks before implementing IAM systems
Robust Architecture: Design systems to minimize vulnerabilities
Compliance Focus: Ensure alignment with relevant regulations
User-centric Design: Aim for usability and minimize workarounds
Continuous Monitoring: Monitor IAM activities for anomalous behavior
Privileged Access Control: Implement PAM for privileged user management
Incident Response: Have a plan in place to handle IAM breaches or failures
Agile Project Management
Key Considerations:
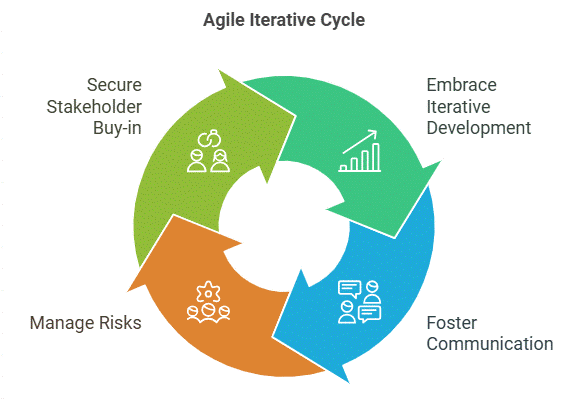
Agile Approach: Embrace iterative development and continuous improvement and be flexible
Communication: Implement a comprehensive communication plan to keep all stakeholders informed
Risk Management: Continuously monitor risks and have mitigation strategies in place
Stakeholder Buy-in: Actively involve stakeholders in all project phases

Agile Project Management
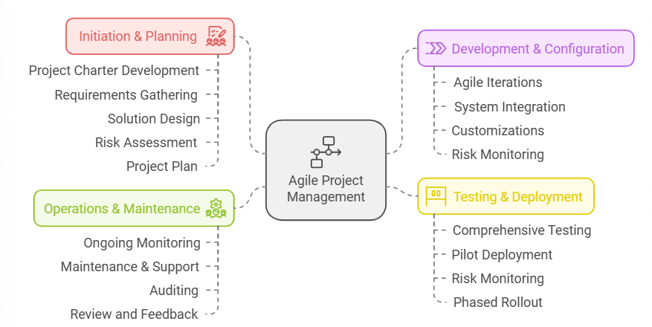
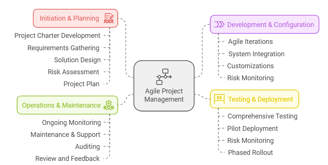
Enterprise-Wide IAM Implementation
Sample, high-level project plan, simply a starting point only and should be heavily customized
Key Considerations:
Agile Approach: Embrace iterative development and continuous improvement and be flexible
Communication: Implement a comprehensive communication plan to keep all stakeholders informed
Risk Management: Continuously monitor risks and have mitigation strategies in place
Stakeholder Buy-in: Actively involve stakeholders in all project phases
Summary of Risk-Focused Research
The research surrounding IAM risks highlights several critical themes:
1. Data Breaches & Unauthorized Access: A primary concern is the risk of data breaches resulting from vulnerabilities in IAM systems or from unauthorized access due to weak access controls. Researchers often analyze real-world data breach incidents to understand the role of IAM failures.
2. Compliance Violations & Fines: Inadequate IAM can lead to non-compliance with regulations such as GDPR, HIPAA, PCI DSS, etc., resulting in significant financial penalties and reputational damage. Research papers often explore the link between IAM practices and regulatory requirements.
3. Operational Disruption & Business Downtime: Poorly designed or implemented IAM systems can disrupt business operations, causing downtime due to login problems or lack of appropriate access. This can severely impact productivity and revenue.
4. Insider Threats: A major risk factor is the potential for malicious insiders to exploit IAM vulnerabilities for unauthorized access or data theft. Research highlights the importance of implementing robust monitoring and privileged access management (PAM).
5. Complexity & Integration Issues: Complex IAM systems are often difficult to manage, creating security gaps due to misconfigurations or inconsistencies. Research emphasizes the need for simplification and standardization of IAM practices.
6. Lack of User Adoption: Poorly implemented IAM that disrupts user workflows often leads to users circumventing the IAM, creating security risks. Research explores usability and user-centric design in IAM.
Source: Google AI Studio Gemini Flash 2.0 Deep Research

brent@projectshop.ca
+1 (416) 805-6335
© 2024. All rights reserved.
< migrate / modernize / innovate >

